Analyst(s): Fernando Montenegro
Publication Date: February 18, 2026
Palo Alto Networks has entered into a definitive agreement to acquire Koi Security for an estimated $400 million. This acquisition targets the “Last Mile” of the modern attack surface: the unvetted browser extensions and AI tools that employees install to boost productivity. By integrating Koi’s technology, Palo Alto Networks is betting that the future of endpoint security lies not in scanning files but in governing the endpoint’s software supply chain.
What is Covered in This Article:
- A $400M acquisition of Koi Security by Palo Alto Networks to secure the modern endpoint.
- The “Productivity Paradox”, where users bypass security to install unvetted tools for efficiency.
- Complementing “Runtime Detection” (EDR) with “Upstream Governance” (Marketplace Control).
- How governing extensions today set the stage for the control plane for Agentic AI tomorrow.
The News: Palo Alto Networks has announced that it has entered into a definitive agreement to acquire Koi Security for an estimated $400 million. Founded in 2024 by Unit 8200 alumni, Koi specializes in securing the expansive ecosystem of binary and non-binary software components, such as browser extensions, AI models, and more. The young company (founded in 2024) made its name following its viral “Darcula” experiment, which exposed critical vulnerabilities in the VSCode Marketplace by successfully infiltrating major enterprises with a benign-looking but surveillance-capable extension. According to the release, Koi’s Wings Risk Engine will be integrated into Prisma AIRS and Cortex XDR, positioning the end users’ browsers and IDEs as the key sensors for governing AI-driven workflows.
No More Playing Koi: Can Palo Alto Networks Secure the Modern Supply Chain?
Analyst Take: One of the most important considerations in modern security is not just the sophisticated adversary breaking down the organization’s defenses, such as firewalls or endpoint protection. Rather, it is the internal friction between rigid security policy and the user’s desperate need for efficiency. According to The Futurum Group’s recent Cybersecurity Decision Makers survey, the single greatest strategic challenge facing organizations is “Balancing strict security controls with user productivity and experience” (see below). This specific friction point is ranked higher than cost, compliance, or even talent shortages. When security controls slow down the workflow, users do not simply stop working. They find a workaround.
Figure 1 – Top Endpoint Security Challenges
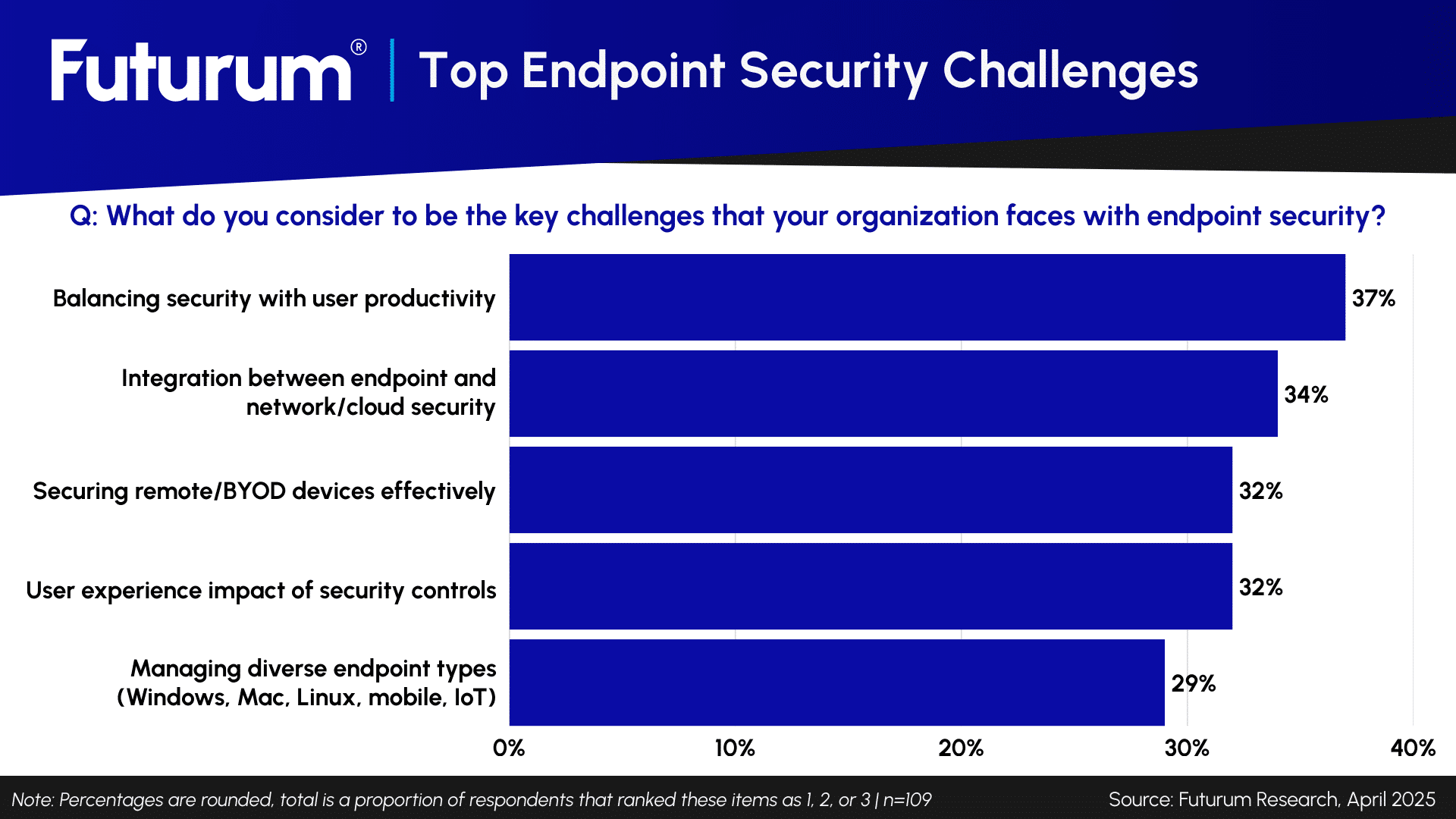
In 2026, that workaround is the marketplace. Developers and knowledge workers, driven by the need for speed, are bypassing IT approval processes to install “Productivity Helpers,” “Code Optimizers,” and “PDF Converters” directly from their browser’s Web Store or the marketplace for their Integrated Development Environment (IDE). These tools appear benign and are often functionally necessary for users to do their jobs, but they effectively act as a shadow supply chain. They operate with high privileges within the browser or the IDE, yet they remain invisible to traditional security tools.
Redefining the Application
We must stop pretending that the “Application” is still a single, compiled executable managed by IT. For the modern worker, the application is a composite environment consisting of the browser, ten to fifteen extensions, and increasingly, an AI model or two, not to mention the coming onslaught of agentic capabilities.
Traditional Endpoint Detection and Response (EDR) tools are excellent at securing the operating system and the executable files. They can see that “chrome.exe” or “edge.exe” is running and that it has a valid signature. However, they often suffer from a fundamental blind spot regarding the components inside that container. They often cannot distinguish between a legitimate extension installed by a developer and a malicious, typosquatted package harvested from a public repository.
This is where Koi aims to provide critical functionality. It shifts the defensive strategy from runtime detection to upstream governance. Rather than waiting for a malicious extension to execute code and trigger an alert, Koi was designed to act as a gatekeeper for the endpoint. It aims to verify the identity, reputation, and integrity of every package, extension, and AI model before they are allowed to be installed. It effectively serves as a firewall for the software supply chain, neutralizing the risk posed by the unvetted marketplace without blocking it entirely.
The Control Plane for the Agentic Future
This acquisition is both a catch-up and a future-proofing play for Palo Alto Networks.
Key endpoint competitors such as CrowdStrike, Microsoft, SentinelOne, and others already have different levels of functionality for deeper inspection of browser extensions. Koi’s acquisition helps Palo Alto Networks implement similar capabilities with a modern, agentless approach that may appeal to many organizations.
While the immediate value lies in securing browser extensions and developer tools, the long-term vision is clearly focused on the emerging Agentic AI economy. An autonomous AI agent is, structurally, just a sophisticated extension with permission to act on the user’s behalf. As agents move from being chat-based bots to autonomous tools installed on endpoints and potentially acting autonomously in marketplaces, the risk profile will mirror exactly what we see with browser extensions today.
By mastering the governance of extension installations now, Palo Alto Networks is building muscle memory and the control plane to govern this more amorphous, autonomous supply chain.
Suitable for a More Collaborative Culture
This offering targets the modern security leader, specifically the CISO and security architecture teams who have evolved beyond the traditional gatekeeper mentality. This buyer still sits firmly within the security organization but possesses a nuanced view of what constitutes an application in the modern enterprise. They understand that the browser and the ecosystem of extensions and agents within it is the new runtime, and they are moving away from blanket blocking policies that drive users toward shadow IT.
These leaders are actively seeking to collaborate with business units rather than obstruct them. Their goal is to shed the “Department of No” reputation by implementing controls that are invisible to the productive user. They are looking for a platform that enables granular governance by eliminating high-risk behaviors while preserving the productivity tools the business demands. This effectively bridges the gap between a strict security posture and operational agility.
What to Watch:
- What is next in the competitive landscape? While competitors increasingly possess browser visibility, watch for them to pivot toward more sophisticated analysis of browser environments and artifacts.
- Can agentless intervention truly be frictionless? The success of this integration depends on enforcing surgical policies without breaking the application and driving users back to shadow IT.
- Who governs the Agent-of-Agents? As autonomous agents begin installing their own dependencies to complete tasks, security must evolve to audit the software’s decision logic.
- Will compliance demand an Agentic Bill of Materials? Organizations may soon require a real-time inventory of every tool, extension, and API that an autonomous agent touches or installs.
For additional information on the acquisition, please refer to the Palo Alto Networks press release.
Declaration of Generative AI and AI-assisted Technologies in the Writing Process: While preparing this work, the author used AI capabilities from both Google Gemini and/or Futurum’s Intelligence Platform to summarize source material and assist with general editing. After using these capabilities, the author reviewed and edited the content as needed. The author takes full responsibility for the publication’s content.
Disclosure: Futurum is a research and advisory firm that engages or has engaged in research, analysis, and advisory services with many technology companies, including those mentioned in this article. The author does not hold any equity positions with any company mentioned in this article.
Analysis and opinions expressed herein are specific to the analyst individually and data and other information that might have been provided for validation, not those of Futurum as a whole.
Other Insights from Futurum:
Governing the Browser: Security’s Next Frontier – Report Summary
Futurum Research: Endpoint Security Impacted by Ownership and Productivity
The Urgency of Securing the Software Supply Chain – Report Summary
As CrowdStrike Buys Seraphic, Is Browser Security Destined to Be Just a Feature?
Author Information
Fernando Montenegro serves as the Vice President & Practice Lead for Cybersecurity & Resilience at The Futurum Group. In this role, he leads the development and execution of the Cybersecurity research agenda, working closely with the team to drive the practice's growth. His research focuses on addressing critical topics in modern cybersecurity. These include the multifaceted role of AI in cybersecurity, strategies for managing an ever-expanding attack surface, and the evolution of cybersecurity architectures toward more platform-oriented solutions.
Before joining The Futurum Group, Fernando held senior industry analyst roles at Omdia, S&P Global, and 451 Research. His career also includes diverse roles in customer support, security, IT operations, professional services, and sales engineering. He has worked with pioneering Internet Service Providers, established security vendors, and startups across North and South America.
Fernando holds a Bachelor’s degree in Computer Science from Universidade Federal do Rio Grande do Sul in Brazil and various industry certifications. Although he is originally from Brazil, he has been based in Toronto, Canada, for many years.







