Analyst(s): Fernando Montenegro
Publication Date: January 15, 2026
CrowdStrike has entered a definitive agreement to acquire Seraphic Security, a strategic move into the rapidly growing browser security market. By securing the session rather than just the endpoint, CrowdStrike aims to close critical gaps on unmanaged devices while addressing the rising complexity of web-based attacks. The acquisition immediately deepens the Falcon platform’s visibility into encrypted browser sessions, building upon existing partnerships and capabilities to deliver comprehensive “in-session” control.
What is Covered in this Article:
- Details of CrowdStrike’s acquisition of Seraphic Security, valued at an estimated $400-420 million.
- Strategic focus on “in-session” runtime protection, securing unmodified browsers to address fraud and misuse in complex web apps.
- Analysis of the “Security vs. Experience” challenge, leveraging Futurum survey data on user productivity.
- Commentary on platform depth, detailing how Seraphic augments CrowdStrike’s existing extension monitoring and browser partnerships.
- Future outlook on browser security consolidation and potential SASE implications.
The News: CrowdStrike has entered a definitive agreement to acquire Seraphic Security, a browser security startup, for an estimated $400-420 million. Seraphic secures unmodified browsers (Chrome, Edge, Safari) via a JavaScript abstraction layer, distinguishing it from competitors that focus on a preferred approach of using proprietary enterprise browsers, often using the Chromium engine. The deal integrates this runtime protection with CrowdStrike’s Falcon platform and identity technology from the very-recently-announced SGNL acquisition to secure SaaS and GenAI interactions. Closing is expected in CrowdStrike’s fiscal Q1 2027.
As CrowdStrike Buys Seraphic, Is Browser Security Destined to Be Just a Feature?
Analyst Take: CrowdStrike’s acquisition of Seraphic Security highlights a long-running but undeniable shift in defensive strategy: the browser is no longer just an application; it is the “operating system” of the modern enterprise. As web applications grow in complexity, they present a dual-threat surface. First, the browser engine itself is a new attack surface, prone to vulnerabilities. Second, and arguably more critical, it is the primary locus for misuse and fraud, which are attacks that rely on manipulating identity and data logic rather than exploiting code. By acquiring Seraphic and coupling it with the rest of the Falcon platform, CrowdStrike positions itself to govern this “high-level” logic layer, securing the interaction between the user and the data, not just the device.
Solving the “Security vs. Experience” Paradox
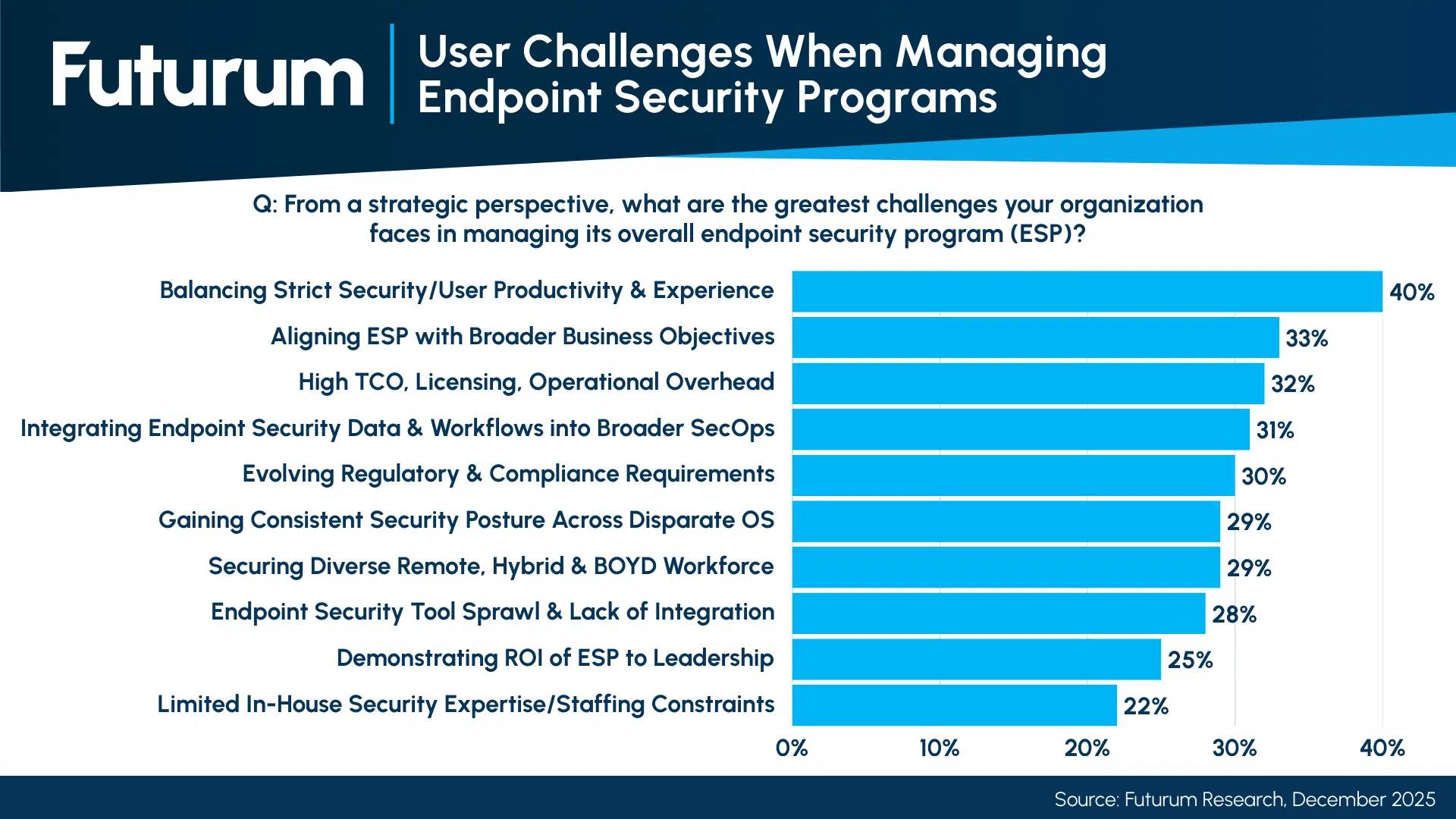
The decision to secure existing browsers (Chrome, Edge) rather than forcing a switch to a proprietary “Enterprise Browser” directly addresses an important market friction point. According to Futurum’s latest Cybersecurity Decisionmaker Survey, “balancing strict security controls with user productivity” is the single greatest strategic challenge facing organizations today when it comes to endpoint security (see figure below). More prescriptive browser isolation tools often fail this test. Seraphic’s approach will position CrowdStrike to secure the browser users already choose, potentially solving the UX dilemma that hinders widespread adoption.
Figure 1: User Challenges When Managing Endpoint Security Programs
Deepening Falcon’s Visibility: Beyond Extensions and Partnerships
CrowdStrike is not starting from zero in this domain. The Falcon platform already possesses capabilities to monitor browser extensions and maintains integrations with both Microsoft Edge for Business and Chrome Enterprise to ingest telemetry. However, Seraphic offers a significant step change in depth. While existing integrations provide excellent policy management and surface-level visibility, they often rely on API limitations. Seraphic’s JavaScript abstraction layer enables CrowdStrike to inspect the encrypted session rendering engine itself. This enables analysts to correlate device-level signals with granular in-session behaviors such as copying and pasting sensitive data into GenAI tools or dynamic phishing attempts, providing a level of runtime control that standard partnerships cannot fully address.
Capturing the “Unmanaged” Greenfield
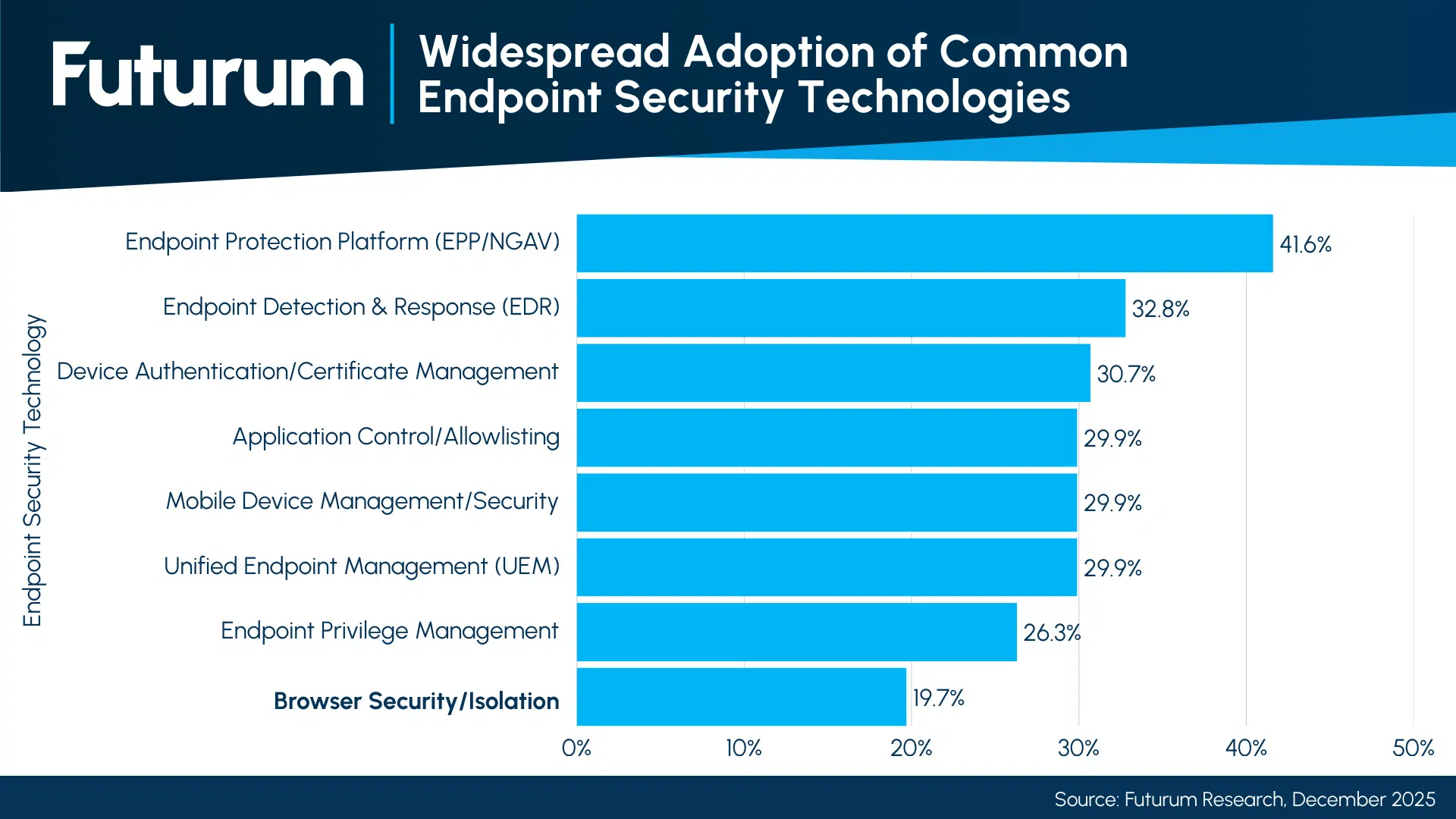
This is also a play for the unmanaged device, such as contractors and BYOD users, where installing a kernel-level agent is impossible. Futurum data shows browser security is still in the early adoption phase, with only 19.7% of respondents reporting widespread deployment. This represents a significant greenfield opportunity for CrowdStrike to extend its visibility to devices it previously couldn’t touch.
Figure 2: Widespread Adoption of Common Endpoint Security Technologies
Consolidation and Future Adjacencies
Finally, this move pressures standalone browser security vendors by commoditizing their core offering into a platform feature. Futurum’s data indicates “improved integration” is a top motivator for vendor consolidation. While this acquisition is primarily about deepening endpoint and identity control, it inevitably brings CrowdStrike closer to the conversation around Secure Access Service Edge (SASE). Although not the primary driver today, possessing a browser-edge security layer gives CrowdStrike the option to encroach on SASE territory in the future, potentially blurring the lines between endpoint protection and network security.
What to Watch:
- Will CrowdStrike formally enter the SASE market? While the current focus is on endpoint and identity, does this browser layer lay the groundwork for a future full-stack SASE offering?
- How will the “Enterprise Browser” market react? Will standalone vendors like Island be forced to pivot or sell as major platforms like CrowdStrike and Palo Alto Networks consume the category?
- Can the integration handle the complexity of modern web applications? As web apps become more intricate, will Seraphic’s JavaScript abstraction layer scale effectively without introducing latency or breaking app functionality?
- Will Google and Microsoft play along? As security vendors patch deeper into the browser session, will Chrome and Edge tighten their ecosystems to block third-party runtime manipulation?
Additional details can be found in CrowdStrike’s press release.
Declaration of Generative AI and AI-assisted Technologies in the Writing Process: While preparing this work, the author used AI capabilities from both Google Gemini and/or Futurum’s Intelligence Platform to summarize source material and assist with general editing. After using these capabilities, the author reviewed and edited the content as needed. The author takes full responsibility for the publication’s content.
Disclosure: Futurum is a research and advisory firm that engages or has engaged in research, analysis, and advisory services with many technology companies, including those mentioned in this article. The author does not hold any equity positions with any company mentioned in this article.
Analysis and opinions expressed herein are specific to the analyst individually and data and other information that might have been provided for validation, not those of Futurum as a whole.
Other insights from Futurum:
Governing the Browser: Security’s Next Frontier – Report Summary
Can CrowdStrike Tackle Standing Privileges with $740M SGNL Acquisition?
CrowdStrike Fal.Con 2025: A Vision and a Path to the Human-Led Agentic SOC
Author Information
Fernando Montenegro serves as the Vice President & Practice Lead for Cybersecurity & Resilience at The Futurum Group. In this role, he leads the development and execution of the Cybersecurity research agenda, working closely with the team to drive the practice's growth. His research focuses on addressing critical topics in modern cybersecurity. These include the multifaceted role of AI in cybersecurity, strategies for managing an ever-expanding attack surface, and the evolution of cybersecurity architectures toward more platform-oriented solutions.
Before joining The Futurum Group, Fernando held senior industry analyst roles at Omdia, S&P Global, and 451 Research. His career also includes diverse roles in customer support, security, IT operations, professional services, and sales engineering. He has worked with pioneering Internet Service Providers, established security vendors, and startups across North and South America.
Fernando holds a Bachelor’s degree in Computer Science from Universidade Federal do Rio Grande do Sul in Brazil and various industry certifications. Although he is originally from Brazil, he has been based in Toronto, Canada, for many years.







