Analyst(s): Fernando Montenegro
Publication Date: February 17, 2026
Proofpoint has acquired Acuvity to extend its data security perimeter beyond the inbox and into the emerging “agentic workspace.” This strategic pivot aims to secure the intent of autonomous AI agents through runtime governance, challenging established vendors and cloud-native startups for control of the enterprise AI gateway.
What is Covered in This Article:
- Proofpoint acquires Sunnyvale-based startup Acuvity to bolster AI security and governance.
- The integration of the RYNO platform to secure the “agentic workspace,” including Model Context Protocol (MCP) servers and locally installed tools like Ollama.
- How Proofpoint is aiming to evolve from a human-centric focus to an agent-centric governance model.
- An analysis of how Proofpoint faces pressure from platform vendors (Microsoft, Cisco, Palo Alto Networks), key SASE providers (Netskope, Zscaler, others), and numerous data/cloud security vendors (Cyera, Wiz, Veeam, Commvault, others)
The News: On February 12, 2026, Proofpoint announced its acquisition of Acuvity, a Silicon Valley-based startup specializing in AI security and governance.
Headquartered in Sunnyvale, California, Acuvity was founded in 2023 by a team of cybersecurity veterans. The company is led by co-founder and CEO Satyam Sinha, who previously co-founded the microsegmentation firm Aporeto (acquired by Palo Alto Networks for $144 million) and served as Vice President of Engineering for Prisma Cloud. He is joined by co-founder and CTO Antoine Mercadal, a fellow Aporeto and Palo Alto Networks alumnus.
Before the acquisition, Acuvity operated as a lean team of approximately 24 employees. The startup emerged from stealth in September 2024, backed by a $9 million seed funding round led by Foundation Capital.
Acuvity’s RYNO platform is designed to provide visibility into “Shadow AI” and to enforce real-time policies for LLM interactions through a specialized AI firewall and runtime inspection. Notably, the technology secures the “agentic workspace” by monitoring emerging Model Context Protocol (MCP) connections and locally installed tools like Ollama. This integration will allow Proofpoint to extend its “human-centric” security model to include autonomous agents, addressing risks such as prompt injection and data exfiltration.
Financial terms of the deal were not disclosed.
Can Proofpoint Secure the Intent of the Autonomous Agent?
Analyst Take: The acquisition of Acuvity marks a necessary and timely strategic move for Proofpoint. It signals a recognition that in the emerging “agentic workspace,” the inbox is no longer the primary perimeter: rather, the data workflow is. By integrating Acuvity’s RYNO platform, Proofpoint aims to expand its Data Loss Prevention (DLP) capabilities to address the non-deterministic nature of Generative AI. While network security vendors focus on the pipeline (securing the connection) and DSPM vendors focus on data at rest, Proofpoint is betting that its historical position in human workflows gives it a unique advantage in securing the payload by understanding not just that an agent is moving data, but why.
From Static DLP to “Semantic” Governance
The potential technical differentiator here is the shift from “Shadow AI” discovery (which is now a commodity) to runtime enforcement. Traditional DLP relies on static rules and regex (e.g., “block credit card numbers”), which often fail against human and, increasingly, non-human attackers using Large Language Models that can rephrase sensitive data into harmless-looking text. Acuvity aims to provide the semantic understanding required to detect intent.
Crucially, Acuvity’s support for the Model Context Protocol (MCP) allows Proofpoint to insert itself into the “read-write” loop of autonomous agents. This is a significant leap beyond the capabilities of a standard proxy, for example. While traditional proxy functionality can block a URL, proxies often struggle to parse the context of a multi-turn agentic conversation without breaking the application. If Proofpoint can successfully layer its Sigma information protection stack on top of Acuvity’s inspection engine, it may be able to offer a “kill switch” for data exfiltration that is context-aware rather than just connection-aware.
The “Digital Insider” and the Stakeholder Gap
This acquisition also offers Proofpoint a narrative bridge to compete with broader platforms: treating the AI Agent as a “digital employee.” Proofpoint is an established vendor in Insider Threat Management (ITM). As agents gain autonomy, the risk of an agent “going rogue” (hallucinating or being jailbroken) mimics the behavior of a malicious insider. By framing AI security as an extension of ITM, Proofpoint can leverage its large installed base and relationships with CISOs to potentially flank competitors such as Palo Alto Networks or CrowdStrike, despite both companies having made AI-specific acquisitions in the past year.
However, the competitive landscape is far broader. Proofpoint is also contending with pressure from at least four distinct vectors:
- The Identity & AppSec Incumbents: This is arguably the stiffest headwind. Okta and CyberArk (now a Palo Alto Networks subsidiary) view AI agents as “Machine Identities” that belong under their governance, not Proofpoint’s. Simultaneously, developer-centric platforms like Snyk are moving to secure MCP servers at the code level, while Lakera (now part of Check Point) has traction as an AI firewall that appeals directly to the engineers Proofpoint may struggle to reach.
- The Email & Human Risk Rivals: Traditional competitors like Abnormal Security and Mimecast (via its acquisition of Aware) are expanding their behavioral detection to cover AI and insider risks, arguing they can secure the “human element” without a separate agent governance tool.
- The Network Gatekeepers: Cloud platform providers like F5 and Cloudflare, among others, are actively securing the AI traffic “pipe” via their own gateway offerings, often bundling this for free with existing enterprise contracts.
- The Data Security Convergence: Proofpoint must compete against dedicated DSPM vendors like Cyera and Wiz, as well as data resilience providers entering the space, including but not limited to IBM, Veeam (via Securiti.ai), and Commvault (via Satori).
Proofpoint’s success will depend on its ability to prove to enterprises that Agent Integrity is not a bottleneck, but the necessary “trust layer” that finally allows them to move their autonomous agents from pilot to production.
Who is the right buyer?
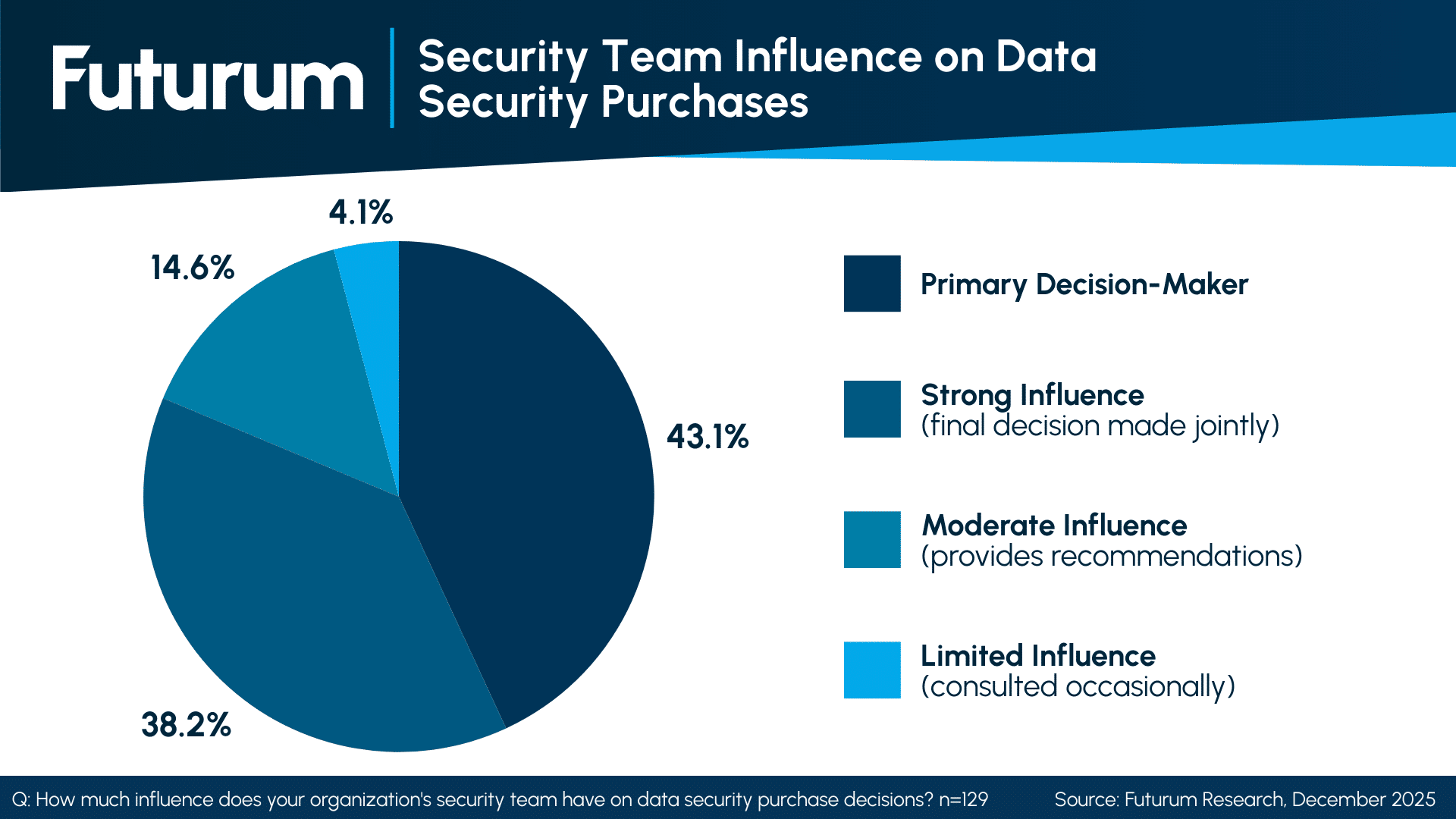
Another aspect that Proofpoint will have to navigate is engaging the right stakeholders within an organization: Does the CISO make the final decision about agent-based security? Recent data from Futurum’s Cybersecurity Decisionmaker survey, fielded during Q4 2025, shows how, in areas such as data security, which is closely related to AI security, the responsibility for data security is increasingly shared between departments.
Figure 1: Security Team Influence on Data Security Purchases
What to Watch:
- Will Proofpoint’s “Human-Centric” branding survive the pivot to “Agentic” security? As autonomous agents become primary actors, Proofpoint must reconcile its identity with a reality where threats are machine-to-machine.
- Will this acquisition trigger a defensive consolidation wave among email security rivals? Competitors like Abnormal Security and Mimecast may be forced to build more capabilities around agent governance.
- Can Proofpoint successfully navigate the shift in buying power to AI engineering teams? As budgets for agentic workflows move away from the traditional CISO, Proofpoint must prove it can sell to the DevOps leaders who may now control the “digital employee” roadmap.
- Will Acuvity’s discovery capabilities expose a “Shadow Agent” crisis? Just as CASB revealed Shadow IT, early deployments may reveal that employees are already using unmanaged agents, forcing a rapid shift in enterprise security priorities.
Further information about the acquisition can be found in Proofpoint’s press release.
Declaration of Generative AI and AI-assisted Technologies in the Writing Process: While preparing this work, the author used AI capabilities from both Google Gemini and/or Futurum’s Intelligence Platform to summarize source material and assist with general editing. After using these capabilities, the author reviewed and edited the content as needed. The author takes full responsibility for the publication’s content.
Disclosure: Futurum is a research and advisory firm that engages or has engaged in research, analysis, and advisory services with many technology companies, including those mentioned in this article. The author does not hold any equity positions with any company mentioned in this article.
Analysis and opinions expressed herein are specific to the analyst individually and data and other information that might have been provided for validation, not those of Futurum as a whole.
Other Insights from Futurum:
How Should We Consider Agentic AI Workflows in Cybersecurity? – Report Summary
Securing Agentic AI Is the Multi-Level Challenge for Security Teams – Report Summary
Was 2025 Really the Year of Agentic AI, or Just More Agentic Hype?
Author Information
Fernando Montenegro serves as the Vice President & Practice Lead for Cybersecurity & Resilience at The Futurum Group. In this role, he leads the development and execution of the Cybersecurity research agenda, working closely with the team to drive the practice's growth. His research focuses on addressing critical topics in modern cybersecurity. These include the multifaceted role of AI in cybersecurity, strategies for managing an ever-expanding attack surface, and the evolution of cybersecurity architectures toward more platform-oriented solutions.
Before joining The Futurum Group, Fernando held senior industry analyst roles at Omdia, S&P Global, and 451 Research. His career also includes diverse roles in customer support, security, IT operations, professional services, and sales engineering. He has worked with pioneering Internet Service Providers, established security vendors, and startups across North and South America.
Fernando holds a Bachelor’s degree in Computer Science from Universidade Federal do Rio Grande do Sul in Brazil and various industry certifications. Although he is originally from Brazil, he has been based in Toronto, Canada, for many years.